Distributing malware with Google images, service workers and vegan Twitter bots
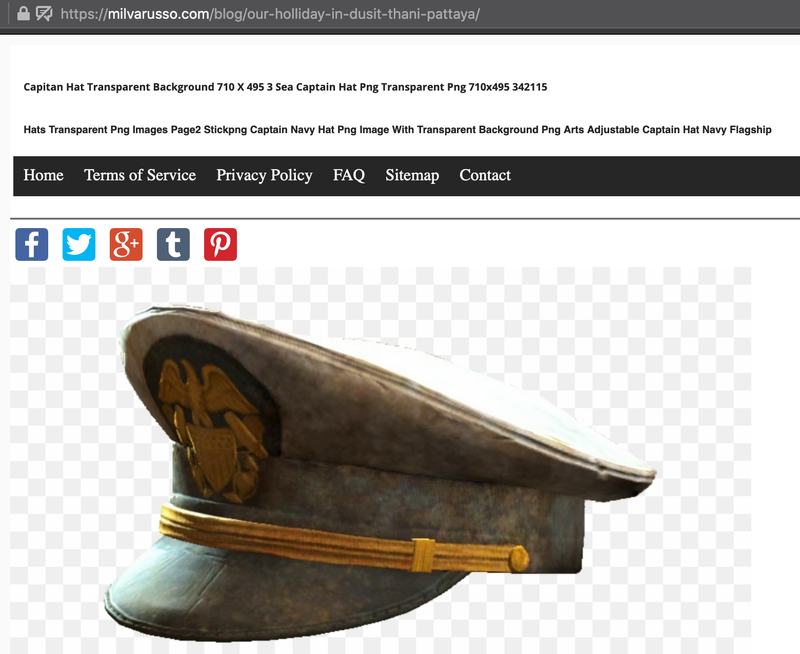
What started with a simple image search for “Skippers hat” quickly turned into investigating a clever malware distribution network utilizing service workers, which is somehow linked to a group of hardcore vegan twitter bots. The hat at the entrance of the rabbit hole was innocent enough:
However, when I clicked on the result I was taken to this page:
A few things about this page interested me:
- It’s the wrong bloody hat
- The URL appeared to be a blog post: https://milvarusso.com/blog/seven-days-at-katathani-phuket-beach-resort/
- Visiting that URL without clicking through Google images takes you to a pretty normal looking site about travelling around Thailand. Not the place you’d expect to find a vector drawing of a skippers hat
- The domain name differed from the one listed on the image result page: Google thought the image existed on
phonebookofgrenoble.xyzbut I was sent tomilvarusso.com
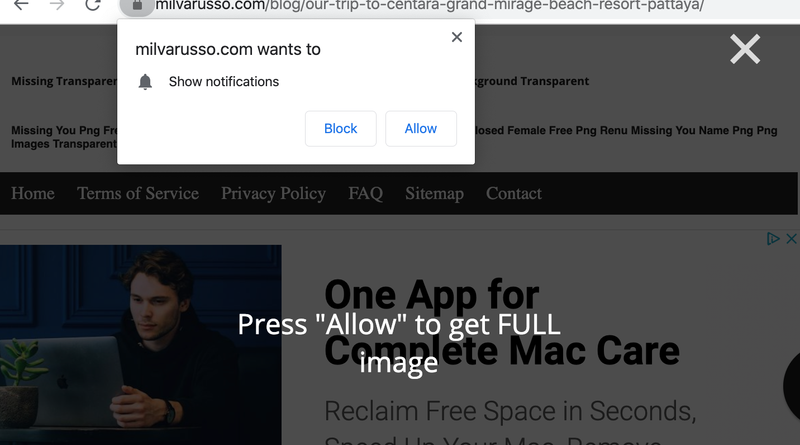
When you visit https://milvarusso.com/blog/seven-days-at-katathani-phuket-beach-resort/ a JS file from a subdomain is loaded: https://forsomeuse.milvarusso.com/?pu=me2tcn3dmm5ha3ddf42dsna (Source). Looking at the script we can see that it creates an overlay and creates a service worker:
const SETTINGS = {
workerName: 'v2max.js',
serverUrl: 'https://feedbase24.com/?push=8bd42aa4-d0bb-4ae1-8e50-3ca22fde562c&s=me2tcn3dmm5ha3ddf42dsna',
background: {
text: "Press \"Allow\" to get FULL image"
// ... lots moreAfter opening the page in Chrome without an adblocker (which apparently prevent the service worker or the overlay from being created) I indeed see:
The overlay tricks users into pressing “Allow” on notifications to view the image. Once the notification permission has been accepted then the service worker (Source) will fetch an endpoint on another domain: https://texterra.me/?endpoint=something&ver=2. This endpoint returns a JSON object that is used to display a notification to the user:
{
"title": "Your Mac is infected?",
"body": {
"body": "Check your Mac for viruses",
"data": { "url": "https://mediabasket.club/..." },
"url": "https://mediabasket.club/...",
"click_action": "https://mediabasket.club/...",
"requireInteraction": true,
"renotify": true,
"time_to_live": 86400,
"vibrate": [600]
}
}So the flow is pretty simple:
- A user clicks an image that’s hosted on
phonebookofgrenoble.xyz phonebookofgrenoble.xyzredirects the user (But not Google) tomilvarusso.com- The user accepts notifications to view the image
- A service worker is installed and will periodically send the user notifications in the background
- The user sees a os-native notification telling them “Your computer is infected”
- They click it, which opens a page that downloads an executable. The page looks official and instructs them to run it
- The user runs the executable and is now infected
This is happening right now, and people are complaining about it.
Honestly it’s pretty clever - Google image links are often the most ephemeral of all searches, you hit the random
site, download the image and go on your way. You wouldn’t remember where the hell you visited milvarusso.com and
it’s not directly connected with phonebookofgrenoble.xyz. Also a non-technical person would have no clue how to
disable these notifications or remove the service worker to stop the notifications.
Network:
There appears to be a large network of these sites. Some others I found:
These are all behind Cloudflare, but some JS files are served from https://forsomeuse.milvarusso.com. This is hosted on
Digital Ocean, and there are some other interesting domains there,
notably the feedbase24.com push URL found in the payloads above.
Twitter bots
If you search for phonebookofgrenoble.xyz you get exactly one result:
— Ultra Eleven (@UltraEleven1) November 15, 2019
When I first found this the tweet was retweeted by the following accounts:
- https://twitter.com/ActivityVegan
- https://twitter.com/turtles_vegan
- https://twitter.com/FerretssV
- https://twitter.com/tale_vegan
- https://twitter.com/HedgehogsVegan
- https://twitter.com/VeganMode1
- https://twitter.com/dragon_vegan
Kind of weird, right? All of those accounts have since been deleted (presumably for being bots), but one is archived in the wayback machine: https://web.archive.org/web/20191013220009/https://twitter.com/VeganMode1. All the accounts where similar to this one - lots of vegan merch for sale and lots of activity.
The only reason I can think of 7 random vegan related twitter accounts to all like and retweet a random
account that is also clearly a bot is if they are related, and if they wanted to
push the credibility of phonebookofgrenoble.xyz and get it indexed quicker by Google.
A few of the other sites I liked above also have a single tweet from rather random, fishy-looking accounts:
Elk Grove Calendar http://t.co/QngxHAIyDD
— CWFC (@CaliforniaWFC) April 30, 2013
— 📚العسيري📚 (@ALAASSIRE) December 11, 2019
Intelligent Automation Wallpaper https://t.co/fglCRg50B6 #MachineLearning #CognitiveComputing #IntelligentAutomation
— Robotic Scientist (@AI_Scientist) November 26, 2019
Conclusion
The way Google now links to images in search results, thanks to the Getty lawsuit, has created an interesting way of distributing malware that is being actively abused by criminals.
There is also an apparent network of twitter bots to push the legitimacy of sites within this network to get them indexed quickly.